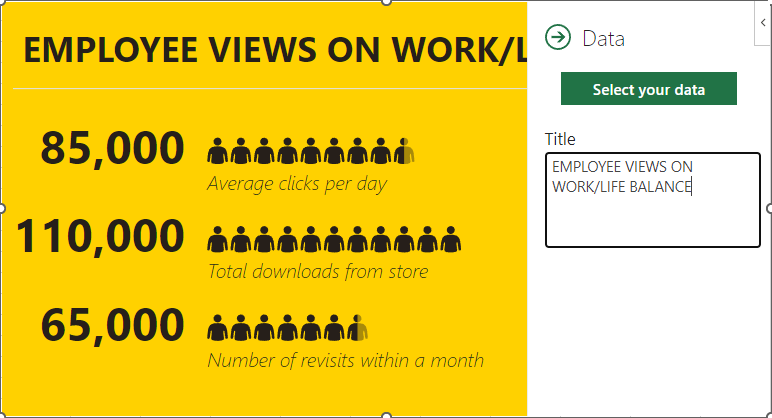
With collaboration playing center stage for most businesses, it’s no small wonder that file sharing is such a priority for SMBs. If you want to establish solid file-sharing practices, you need the right solutions. Today, we want to explore four ways you can establish an efficient and secure file-sharing platform.
Share with the Cloud
The cloud feels tailor-made for collaboration and file sharing.
With the ability to access files anytime, anywhere, collaboration can occur whenever and wherever is most convenient. All you need is an Internet connection and an account. Cloud-based solutions also often come with security measures that mitigate data theft and loss, so they’re not just functional; they’re also secure.
The cloud should be your go-to if you want a solution built for multiple-user collaboration.
Implement an Enterprise File Sharing Platform
Power users of file-sharing platforms can also implement an enterprise-sharing platform.
This is especially helpful for those who need to share files outside of their organization. It provides more security and functionality to control data flow. Furthermore, these platforms offer a centralized location to store and share files, making them easier to secure than other tools.
With advanced security measures like encryption and access control, you’ll never be left wanting for security.
Structure Your File Names
File naming systems offer surprising benefits for file-sharing purposes.
For one, they’re more efficient, as they will allow your team to find files more easily. This strategy clears up potential errors before they even occur, especially for those who work with a lot of files. Collaboration is fueled by efficiency, after all, and anything you can do to make it easier will be welcome with your team.
A good naming convention can also make your systems more searchable, an additional plus.
Back Up Your Files
No matter how much you prepare, accidents and unplanned incidents can happen at any time.
A backup plan will go a long way toward mitigating the damage done by these unexpected situations. Your file-sharing system should be hooked up to your backup plan to fight back against corruption, deletion, or theft. You never know when it might come in handy, and you know what they say: better to have it and not use it than not have it at all.
Plus, you might have some compliance obligations to adhere to, so it never hurts to be prepared.
File sharing is hard, but we make it easy. Call us today at (604) 513-9428 to learn more.